Glacier
Features
Network services
Glacier combines several key network related functions in one package, offering a lot of flexibility. It might look a bit daunting at first, but it is actually not too difficult to grasp the basic concepts. The basic services a Glacier server provides in a network infrastructure are:
- Port forwarding, network services are provided on so-called sockets, Glacier accepts connections on its own sockets and transparently forwards these requests to other network servers.
- Firewall, if you want to exclude a range of computers from using a network service, you can define access rules, ACLs, to selectively grant or deny access to a service based on several criteria, see the firewall page for more information.
- Connection logging, if you ever wanted to determine how many connections are made on a network service, where they originated from and what time and data-transfer they required, Glacier can provide this service without any modifications.
- Load balancing, whether you have several servers offering an identical service or you want to scale your application by using redundant hardware, Glacier provides a transparent load balancing service.
- Traffic shaping, Glacier allows you to limit the rate at which data flows in or out on a per-connection basis, so you can actively guarantee a certain Quality of Service.
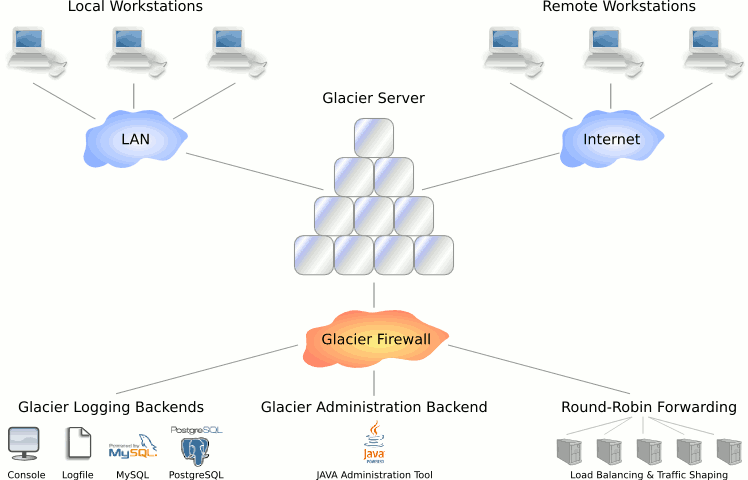
Graphical overview
This graphical overview shows where Glacier fits into your existing network infrastructure, for a detailed explanation of what happens, look at the paragraph Technical overview just below the figure. The technical overview will fill you in on the details regarding the inner workings of Glacier's features, connection management and logging.
Technical overview
Once the Glacier engine is configured properly and is up and running, it will accept incoming TCP/IP connections on its listening sockets. Listening can be limited to physical network interfaces or bound to specific IP addresses if desired, this gives you a basic form of protection as connections on other interfaces will not be acceptde in the first place.
Once a connection attempt is made on a listening socket, the built-in firewalling component is activated to check whether or not the connection should be validated, there are several matching criteria available which can be chained together in an access control list (ACL) to establish a fine grained security control. All incoming connections, both allowed and disallowed, are logged to one or multiple logging backends if desired.
Disallowed connections are dropped immediately without any apparent sign, intruders have no indication why their connection was refused. The connections attempts that are allowed however, are accepted and will be either forwarded to a predefined list of network servers in a round-robin fashion, or will be connected to the internal Glacier administration backend.
Successful connections are constantly updated in the connection logging backend with details on the total connection time, amount of data transferred and the network addresses involved. The connection log data can easily be aggregated and turned into automated reports.
Feature overview
For a detailed list of features, read the following detailed feature pages, they contain screenshots and detailed lists of the core functionality: